A Story about Ransomware Detection and Prevention for an Atlanta Real Estate Firm
This is the story of how cyber criminals in China attempted to take down and extort for ransom an Atlanta Real Estate Firm, how the Boost IT team reacted, and what we can learn from it — ransomware prevention in 2020.
How The Ransomware Hit?
It was Monday, January 7th; the first full week after the holidays. The day began like any other Monday — we gathered over coffee, discussed the fun things we did over our weekends, and had our weekly team meeting to review our client environments. A ticket had come in over the weekend that there was some unusual activity on a client’s servers, and that there was a jump in hard drive activity.
Next was a series of frantic incoming phone calls followed by shock as the gravity of the situation sank in. The day I had been dreading since I founded the company in 2000 was finally here — a client that had repeatedly refused our security recommendations had a full-fledged ransomware attack underway.
Can Ransomware Be Prevented?
In the best cases, our managed security services, when used together, will drastically reduce chances of infection. In fact, our clients that use our full suite of security services have never gotten ransomware. In the worst cases, the bad guys succeed, data is lost, and ransoms are paid out. Fortunately for us, we were well prepared because our client used our rock-solid, cloud-based disaster recovery system so data loss was minimized.
How We Reacted?
Shut it down
The first thing we did once we confirmed the attack was to have everyone power off their workstations. Once ransomware compromises one machine it immediately spreads to the rest of the network. And even with backups in place, recovery takes time. Restoring a single machine can take 1-2 hours and when handling dozens of machines that can easily turn from hours into days.
Search & Analyze
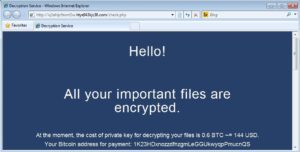
With everything powered off, we started slowly checking each server one by one, and taking samples of the encrypted files so we could send them out for analysis. After submitting the samples to IT Security Researchers we quickly discovered we were dealing with something incredibly nasty: The Dharma -Adobe variant of Ransomware (.cezar family of attacks). This strain is extremely problematic.
Only 1 in 67 anti-virus engines could detect the ransomware
In fact it successfully made its way through their Cisco Meraki Firewall with Advanced Security License, the email security filtering, Microsoft Office 365 mail scans, and past their anti-virus protection.
Put in the time
Even with recent backups available, checking each system individually, completing the restores, and testing to determine which backups weren’t compromised, we watched in real-time as Chinese cybercriminals attempted to login to their servers (we blocked some 7,000 attempts per hour at the height of it). It took people on our team in excess of 100 hours of work that week. It was 14+ hour days and extremely stressful. Brent Tibbetts went above and beyond showing up early and staying late.
Summary Of The Ransomware Attack
- We shut down all workstations before any systems were encrypted and before we got the ransom demands.
- Our client lost 1-2 days of data (Chinese hackers infected the systems but waited a few days to detonate the payload, so we chose to restore from a backup image taken when we knew 100% of the data was unaffected.)
- Our client had only a single day of complete downtime, followed by another couple days of interrupted workflow as we got them up and running on temporary systems while we rebuilt the infrastructure.
- Our team put in 12-14 hour days all week working round the clock to recover from backups and prevent further attacks.
- We learned that Cybersecurity user training is more critical than ever (stay tuned for an email with cybersecurity tips as well training offerings for clients not already using our preferred eLearning platform: KnowBe4)
- We saw firsthand how valuable proper disaster recovery backups are; a file/folder backup is not enough if you want to be able to recover from an attack swiftly. Without recent system images of the servers the backup could have taken 1-2 weeks to rebuild all the infrastructure rather than a day.
- We want to remind our clients just how important good passwords are. If you don’t have a password policy, read this article on How to Create a Strong Password.
A big thank you goes out to our clients for their patience and understanding during the attack. It was a huge productivity loss with their whole office not being able to work. No one yelled or made unreasonable demands on our team. We stayed optimistic, worked together, and ensured a smooth recovery.
Thanks,
Russell Shulin
Founder & Chief Client Success Officer
Boost IT, LLC
If you’d like to stay informed of cybersecurity news and ransomware prevention measures, sign up on our Contact page.
For more info on how the Dharma Ransomware variant works:
https://latesthackingnews.com/2018/08/13/new-variant-of-dharma-ransomware-discovered/