Do you know the one I.T. question you should be asking?
This question is directed at you. Whether you are an individual trying to secure your digital footprint or an employee /owner working for a business, do you know the one I.T. question you should be asking? We do, and we want you to know it and know how to solve for it. The one I.T. question you should be asking is: How can you prevent ransomware? In this post, Boost IT shares 5 tips on how to prevent ransomware.
The Current State of Ransomware
Virus.
Malware.
Phishing.
The dark web.
Cyber attack.
Ransomware.
Everywhere you look, I.T. security buzz words appear. LifeLock commercials about identity theft, to the latest computer popup reminder that your antivirus software needs to be upgraded, the theme of “is my information secure?” seems to resurface.
Grey’s Anatomy even dedicated its winter finale to ransomware. Hackers breached the hospital’s practice management and EMR system causing anything connected to the network to shut down; computers, electronic charts, patient monitors, labs, testing equipment, phones. The message read:
“Hello, Grey / Sloan Memorial. Currently, we control your hospital. We own your servers…your systems…your patient’s medical records. To regain access to your medical records, you need an encryption key…which only we have. You will need to pay us exactly 4,932 bitcoin to retrieve the key. Failure to pay this ransom in a timely manner will cause your records to be destroyed and your systems to be rendered inoperable.”
The hospital was given a deadline to pay the ransom. Shonda Rhimes appropriately named Grey’s Anatomy Season 14, Episode 8: Out of Nowhere. Fitting, isn’t it?
It’s easy to believe that hackers come out of nowhere.
But the reality is that hackers are everywhere, growing more sophisticated, hovering in search of weak spots that need to be secured.
While real-life authorities advise not to pay such ransoms, we acknowledge that it is a difficult decision when a life, or one’s livelihood is on the line. Ten to twenty years ago, hospitals and businesses were using paper charts and files. Today, however, nearly everything runs on the network.
Ransomware isn’t limited to TV drama. Attacks happen daily and the FBI reports that they are on the rise.
Most systems that are vulnerable to ransomware lack a layered I.T. security approach.
The city of Atlanta was faced with a similar ransomware scenario when systems were shut down by hackers requesting $51,000. The attack affected systems ranging from law enforcement, to the city water department, municipal courts, and more. The city has worked diligently to restore, but the threat is very real.
According to the FBI, ransomware is the fastest growing malware threat. Since 2016, more than 4,000 ransomware attacks occur daily, targeting individual users to a variety of businesses from hospitals, to schools, government, SMB and private corporations.
What is ransomware?
Ransomware is a form of malware. Hackers hold your system hostage in exchange for a ransom amount that is to be paid within a certain amount of time. Ransomware can shut down your entire network and bring business to a halt. If the ransom is not paid, your data is deleted. However, if you do pay the ransom, there are no guarantees that your system will be restored without additional malware infections.
How do we solve for ransomware?
The answer is different for an individual versus a business.
For an individual, we recommend signing up for a program called Webroot. Webroot is a cybersecurity and threat intelligence service. Their antivirus software runs on your computer and does a good job of protecting your computer with very little weight to it.
For a business, there are five things that every business needs to address how to prevent ransomware.
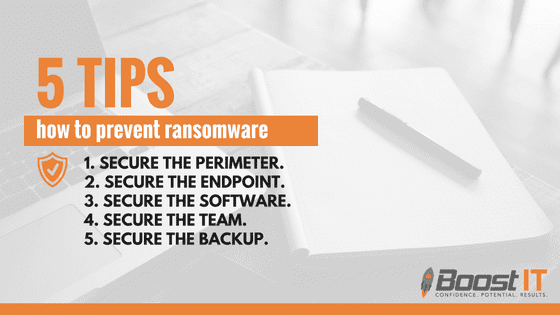
5 Tips on How to Prevent Ransomware for Businesses
1. Secure the Perimeter.
The first layer of prevention is the perimeter. You need a device at the single point of origin where the data comes in the network that protects the entire network, including Wi-Fi. Securing the perimeter is like installing an alarm system at your office – if anything is breached, you have a reaction system in place and receive an alert to act.
2. Secure the Endpoint.
The second layer of protection from ransomware is securing the endpoint. Software should be loaded on each device within the network so that I.T. can monitor, detect and contain harmful activity.
3. Secure the Software.
Third, make sure all applications on machines are updated with the latest version and apply security patches. Securing the software is an important layer because it is designed to update, fix and improve your software by applying patches or bug fixes that improve security, usability and performance.
4. Secure the Team.
While we can create layers of I.T. security to protect the systems that are in place, you also must plan and anticipate user error. Thus, securing your end users and training for ransomware prevention is extremely important.
Ransomware often finds its way into the system via social engineering and/or phishing attempts. An attack may arrive in the form of an innocent email instructing an employee to reset their password, click a link, or open an attachment. Most unassuming victims believe they are resetting a password to increase security. Instead, they fall victim to a ransomware infection. These traps were created to target end users.
Keep these questions in mind when considering how to prevent ransomware by securing end users:
- Do users know how to identify phishing?
- Can users recognize an email that is fake?
- Are we using complex passwords?
- Does each user have their own rather than a shared login?
- Does each user know not to reuse the same password across different platforms?
- Do employees keep passwords secure and out of sight rather than on a sticky note by the computers?
Therefore, anticipating common mistakes and re-training your team to increase network protection is one of the most important steps in preventing ransomware.
5. Secure the Backup.
If for some reason there is a breach or failure in the first 3 layers, securing the backup means that you have a ransomware-resistant backup & disaster recovery system in place. And don’t forget to discuss your expected recovery time with your IT group ahead of time. If you don’t have a recovery time objective (RTO), watch our video on backup and disaster recovery.
In this ransomware scenario, you would have two options: either delete all of the locked down data and restore it from clean backups, or spin up a clean copy of your entire server. Thus, the goal is to restore the system to a point in time prior to the breach.
Summary: How to prevent ransomware
In summary, when planning on How to prevent ransomware, whether you are an individual or a business, make sure your I.T. security has layers.
- 1st Layer = Secure the Perimeter.
- 2nd Layer = Secure the Endpoint.
- 3rd Layer = Secure the Software.
- 4th Layer = Secure the Team.
- 5th Layer = Secure the Backup.
The first four layers are preventative measures. When combined, these security layers significantly reduce the risk that a user’s mistake will result in a breach. The final layer, securing the backup, is the last resort.
To prevent ransomware, begin by planning against the worst-case scenario. As businesses grow more complex and rely more on technology, ransomware is becoming more prevalent. With the proper security layers in place, your I.T. group has multiple opportunities to remain on the offense.
Do you have more questions on preventing ransomware at home or at work? Let us know.
Take a quick Boost IT Cyber Security Self-Assessment for businesses to reduce your security risks.